Cyber Security - Cryptographie
Is the science of securing information by transforming it in such a way as to make it unreadable to any unauthorized person. It uses algorithms to encrypt data, making it accessible only to those who possess the decryption key.
- Download the program

Flexible 100% online training
Start your new career at any time! Available part-time? No problem, study at your own pace.

Professional projects
You will develop your professional skills by working on concrete projects inspired by business reality. No problem, study at your own pace.

Personalized support
Benefit from weekly mentoring sessions with a business expert.

Earn certificates and diplomas
Earning certificates and degrees can enhance your career, broaden your horizons, and provide you with increased personal satisfaction.
- Preview
- Projects
- Accompaniement
Objectives of Cryptography training
Operational objective:
Know how to master the development of enriched cryptosystems.
Educational objectives:
At the end of Cryptography training, you will have acquired the knowledge and skills necessary to:
- Understanding the current and future challenges of cryptography
- Understanding the theoretical and practical difficulties surrounding the deployment of these technologies
- Complete your knowledge with new primitives
- Consider the possibilities offered by modern cryptosystems
Who is this training for?
Audience :
This Cryptography course is primarily aimed at research engineers and security experts/CSOs.
Prerequisites:
To follow this Cryptography training, it is necessary to know the nature and operation of digital signature algorithms, hybrid encryption and hash functions.

A pedagogy based on practice
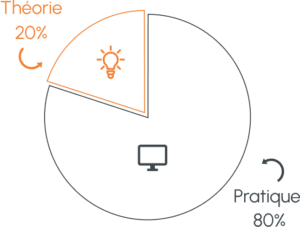
- Acquire essential skills by validating professional projects.
- Progress with the help of a professional expert.
- Gain real know-how as well as a portfolio to demonstrate it.
Cryptography course content:

Foundations:
Reminders of the theoretical bases: proven security, hypotheses (RSA, DLP, factorization, PRP/PRF), adversarial models, elliptic curves, etc.
Limitations and difficulties of existing cryptosystems
Some examples: RSA and ECDSA
Set the security level




Towards homomorphism:
First homomorphisms: RSA, Paillier
Couplings on elliptic curves and applications (MOV, BLS, IBE)
Bilinear groups
Euclidean lattices, their applications (LLL, FHE, mmaps) and hypotheses (SVP, LWE)
Applications of homomorphism (ABE, FE, MPC…)
Grover and Shor's Quantum Algorithms




Beyond Quantum
Isogenies of elliptic curves (SIDH, CSIDH)
Cryptography based on codes (McEliece), polynomials and hash functions (Lamport)
Individual and privileged supervision.
- Benefit from weekly individual sessions with an expert mentor in the field
- quickly in your projects thanks to its excellence in sharing its know-how




The Empire Training community
- Count on a close-knit community of students ready to help you 24/7.
Online pre-registration
Please fill out the form
Please fill out the form
How does an Empire Training course work?
From the chosen training to their entry into their new career, our students recount each stage of their experience and the support they received.