Cyber Security - Firewall
A firewall is a network security device that monitors and controls incoming and outgoing traffic based on predefined security rules. It acts as a protective barrier, preventing unauthorized access while allowing legitimate communications.
- Download the program

Flexible 100% online training
Start your new career at any time! Available part-time? No problem, study at your own pace.

Professional projects
You will develop your professional skills by working on concrete projects inspired by business reality. No problem, study at your own pace.

Personalized support
Benefit from weekly mentoring sessions with a business expert.

Earn certificates and diplomas
Earning certificates and degrees can enhance your career, broaden your horizons, and provide you with increased personal satisfaction.
- Preview
- Projects
- Accompaniement
Firewall Training Objectives
Operational objective :
Know how to identify and eliminate malware before it spreads to your information system.
Educational objectives :
At the end of Malware training, you will have acquired the knowledge and skills necessary to:
- Know the different malwares
- Identify malware
- Implement adequate countermeasures
- Learn how to use system inspection tools
Who is this training for?
Audience :
Any computer scientist with knowledge of basic computer security concepts.
Prerequisites:
Knowledge of basic computer security concepts is necessary

A pedagogy based on practice
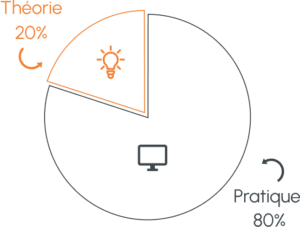
- Acquire essential skills by validating professional projects.
- Progress with the help of a professional expert.
- Gain real know-how as well as a portfolio to demonstrate it.
Firewall Course Content:

Attacks
Target of attacks
Categories
Attack tools
Method and types of attacks
Who to protect yourself from
Examples of attacks
Need for a global approach







Firewall: Concepts
What is a Firewall?
Firewall: Basic type
IP Firewall: Typology
Overall architecture
Stateless Firewall
Stateful Firewall
Application Firewall
Reverse proxy
Multi-level firewall
Protection level
Example of treatment







Firewall: main functions
Packet Filtering: Overview
IP Packet Filtering
Static/dynamic filtering
Filtering by proxy servers
Application firewall (proxy)
Example of proxies
Reverse proxy







Firewall: Other features
NATAnti-spoofingVPN
Authentication
Providing a RADIUS server
Application of ACLs (Access Control List)
Logging (log, alert, audit)
Events that can saturate firewall logs
High availability







Firewall: Architecture and deployment
Elements of an Architecture
Filtering router
Bastion Mode
Stateful Firewall with Proxy
Stateful Firewall with DMZ
DMZ: typologiesMode
Extended DMZ
Firewall with DNS
Architectural study







Firewall: Administration
Technical issues to be resolved
Operations Management
Continuity of service
Individual and privileged supervision.
- Benefit from weekly individual sessions with an expert mentor in the field
- quickly in your projects thanks to its excellence in sharing its know-how




The Empire Training community
- Count on a close-knit community of students ready to help you 24/7.
Online pre-registration
Please fill out the form
Please fill out the form
How does an Empire Training course work?
From the chosen training to their entry into their new career, our students recount each stage of their experience and the support they received.