Cyber Security - Public Key Infrastructure
Is a cryptographic key management system, which enables the issuance, distribution and verification of digital certificates to secure communications and authenticate users online.

Flexible 100% online training
Start your new career at any time! Available part-time? No problem, study at your own pace.

Professional projects
You will develop your professional skills by working on concrete projects inspired by business reality. No problem, study at your own pace.

Personalized support
Benefit from weekly mentoring sessions with a business expert.

Earn certificates and diplomas
Earning certificates and degrees can enhance your career, broaden your horizons, and provide you with increased personal satisfaction.
- Preview
- Projects
- Accompaniement
Training Objectives: Public Key Infrastructure
Educational objectives:
Know how to master PKI principles and implementation.
Educational objectives:
At the end of PKI training you will have acquired the knowledge and skills necessary to:
- Technologies and standards (coarse-grained cryptography)
- Implementations: architectures, integration issues (organization of a PKI, certificate format, sticking points)
- Organizational aspects and certifications
- Legal requirements: electronic signature, recovery keys, use, export / international use
- The three types of tools on the market: the Microsoft Certificate Server offering, the IDNomic commercial offerings and the Open Source offering (EJBCA).
Who is this training for?
Audience :
This training is aimed at Architects, Project Managers, Security Managers/RSSIs with a technical orientation, Senior Developers, Senior System and Network Administrators.
Prerequisites:
To follow this course optimally, you must have initial training or proven experience in IT, such as knowing how to launch a command line, having notions of API and knowing how IP networks work.

A pedagogy based on practice
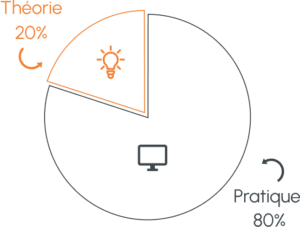
- Acquire essential skills by validating professional projects.
- Progress with the help of a professional expert.
- Gain real know-how as well as a portfolio to demonstrate it.
PKI Course Content:

Technique and cryptography:
Cryptographic primitives synthesisGeneral framework: History, Definitions
Mechanisms: Encryption, condensate, MAC, Modes
Common assemblies: signature, symmetrical & asymmetrical combination, session key, IV
Cryptographic attacks: from brute force to quantum cryptanalysis
System attacks: “side channel”, “man in the middle”, attacks on key management
Secrets Management: HSM Key Management, Software Containers
ANSSI/NIST/ECRYPT Recommendations
The need for PKI






Architecture and integration:
PKI-X Architecture: CA/Sub-CA/RA
Common architectures: concrete variations of roles
Defining a certification policy and a security policy
Implementation details: Key generation and certificate issuance, revocation, key dissemination
PKI typology: Internal for dedicated use Internal transversal External dedicated (PKI As A Service) External shared (Certificate As A Service), embedded PKI
Organizational Aspects: Key processes, control.
Certification: ETSI requirements: 102042, 101456, 102023 RGS, PSC requirements






Managing a PKI project
Pre-studies:
– Summary of the need
– Definition of the technical infrastructure
– Definition of the organizational component
Framing workshop
– Conducting a framing workshop
– Framing support
Functional specifications
– Expressions of needs
– Functional specifications
Studies of solutions and comparisons
– Microsoft (ADCS)
– Open (EJBCA)
– Commercial (IDNomic)






Implementing a PKI:
Presentation of an Open Source solution, EJBCA
Introducing a commercial solution, IDNomic
Microsoft Certificate Services Overview
Product Architecture Overview
Demonstration of common use:
– Setting up and configuring the Root CA
– Setup and configuration of the RA
– Implementation of the trust model – Key generation
– Certificate, Certificate Options
– Revocation, publication
Token generation






Legal aspects and perspectives:
Legal aspectsElectronic signature: legal value, framework…
Usage regulations: limitations, escrow (trusted third party), export
International use.
Individual and privileged supervision.
- Benefit from weekly individual sessions with an expert mentor in the field
- quickly in your projects thanks to its excellence in sharing its know-how




The Empire Training community
- Count on a close-knit community of students ready to help you 24/7.
Online pre-registration
Please fill out the form
Please fill out the form
How does an Empire Training course work?
From the chosen training to their entry into their new career, our students recount each stage of their experience and the support they received.